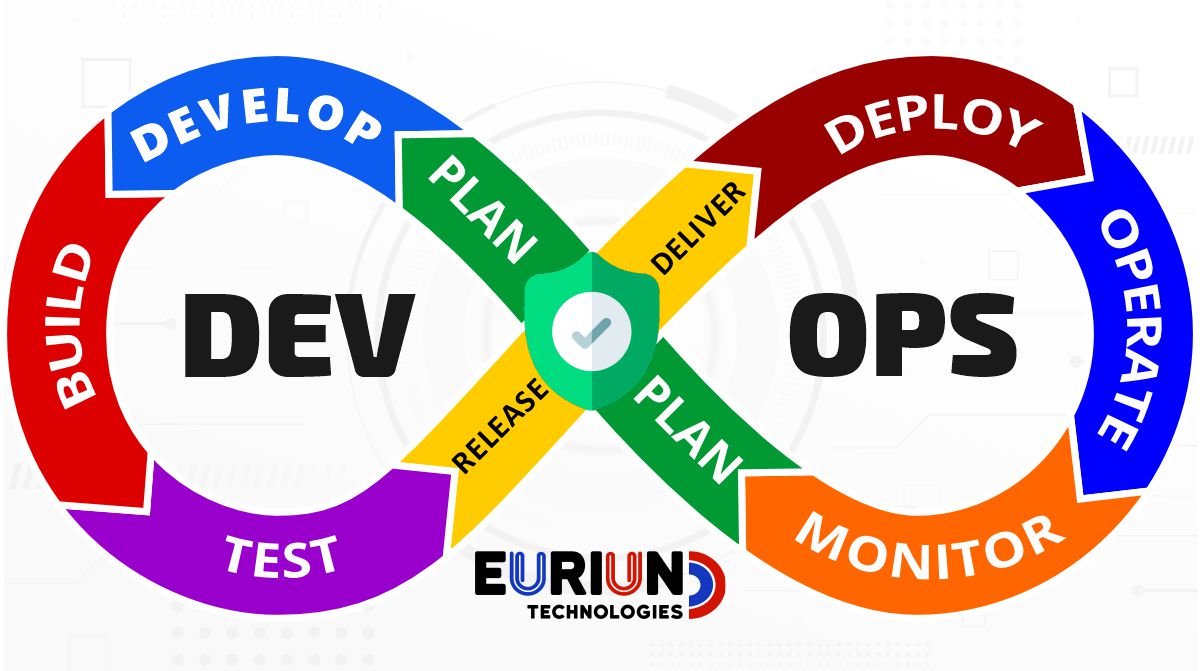

Plan Phase
The Planning phase supports software development planning, which includes configuration management planning, change management planning, project management planning, system design, software design, test planning, and security planning.
Develop Phase
The Development phase supports the development activities that convert requirements into source code. The source code includes application code, test scripts, Infrastructure as Code, Security as Code, DevSecOps workflow scripts, etc.

Build Phase
The Build Phase performs the tasks of building and packaging applications, services, and microservices into artifacts. It also includes generating application documentation, copying files like libraries or icons to the appropriate locations, and creating a distributable file such as a zip file.

Test Phase
The Testing Phase involves continuous testing across the software development lifecycle. Test activities may include, but are not limited to, unit test, functional test, integration test, system test, regression test, acceptance test, performance test, and variety of security tests. All tests start with test planning and test development, which includes detailed test procedures, test scenarios, test scripts, and test data.

Release & Deliver Phase
In the release and deliver phase, the software artifacts are digitally signed to verify that they have passed build, all tests, and security scans. They are then delivered to the artifact repository. The content of the artifacts depends on the application. It may include, but is not limited to, container images, VM images, binary executables (such as jar, war, and ear files), test results, security scan results, and Infrastructure as Code deployment scripts.

Deploy Phase
In the Deployment Phase, the two major deployment options include virtual machines and software containers.
In a Virtual Machine Deployment, the virtualization manager manages the virtual compute, storage, and network resources.
In a Container Deployment, the container manages the configuration tasks, such as instantiation, scaling, monitoring, and rolling updates.

Operate Phase
The Operation phase involves system scaling, load balancing, and backup. Load balancing monitors resource consumption and demand, and then distributes the workloads across the system resources. Scaling helps dynamic resource allocation based on demand.
Application deployment must have proper load balancing and scaling policies configured. During runtime, the management layer will continuously monitor the resources.

Monitor Phase
The Monitoring Phase involves the collection and assessment of key information about the use of the application to discover trends and identify problem areas. Monitoring spans the underlying hardware resources, network transport, applications / microservices, containers, interfaces, normal and anomalous endpoint behavior, and security event log analysis. It continuously inventories all system components, monitors the performance and security of all components, and logs application and system events.
| wdt_ID | AID | Phase | Activity | Description | Data Required |
|---|---|---|---|---|---|
| 1 | 1 | Plan | DevSecOps ecosystem design | Design the DevSecOps process workflows that are specific to this project | - Change management process; - System design; - Release plan & schedule. |
| 2 | 2 | Plan | Project team onboarding planning | Plan the project team onboarding process, interface, access control policy | Organization policy |
| 3 | 3 | Plan | Change management planning | Plan the change control process | - Organizational policy; - Software development best practice. |
| 4 | 4 | Plan | Configuration identification | Discover or manual input configuration items into CMDB; Establish system baselines | - IT infrastructure asset; - Software system components (include DevSecOps tools); -code baselines -document baselines. |
| 5 | 5 | Plan | Configuration management (CM) planning | Plan the configuration control process; Identify configuration items | - Software development, security and operations best practice; - IT infrastructure asset; - Software system components. |
| 6 | 6 | Plan | Software requirement analysis | Gather the requirements from all stakeholders | - Stakeholder inputs or feedback; - Operation monitoring feedback; - Test feedback. |
| 7 | 7 | Plan | System design | Design the system based the requirements | Requirements documents |
| 8 | 8 | Plan | Project planning | Project task management Release planning | |
| 9 | 9 | Plan | Risk management | Risk assessment | - System architecture; - Supply chain information; - Security risks. |
| 10 | 10 | Plan | Threat modeling | Identify potential threats, weaknesses and vulnerabilities. Define the mitigation plan | System design |
| 11 | 11 | Plan | Database design | Data modeling; database selection; Database deployment topology | System requirement; System design |
| 12 | 12 | Plan | Design review | Review and approve plans and documents | Plans and design documents; |
| 13 | 13 | Plan | Documentation version control | Track design changes | Plans and design documents; |
| 14 | 14 | Develop | Application code development | Application coding | Developer coding input |
| 15 | 15 | Develop | Infrastructure code development | -System components and infrastructure orchestration coding -Individual component configuration script coding | Developer coding input |
| 16 | 16 | Develop | Security code development | Security policy enforcement script coding | Developer coding input |
| 17 | 17 | Develop | Test development | Develop detailed test procedures, test data, test scripts, test scenario configuration on the specific test tool | Test plan |
| 18 | 18 | Develop | Database development | Implement the data model using data definition language or data structure supported by the database; Implement triggers, views or applicable scripts; Implement test scripts, test data generation scripts. | Data model |
| 19 | 19 | Develop | Code commit | Commit source code into version control system | Source code |
| 20 | 20 | Develop | Code commit scan | Check the changes for sensitive information before pushing the changes to the main repository. If it finds suspicious content, it notifies the developer and blocks the commit. | Locally committed source code |
| 21 | 21 | Develop | Code review | Perform code review to all source code. Note that pair programming counts. | Source code |
| 22 | 22 | Develop | Documentation | Detailed implementation documentation | User input; Developed Source Code |
| 23 | 23 | Develop | Static code scan before commit | Scan and analyze the code as the developer writes it. Notify developers of potential code weakness and suggest remediation. | Source code; known weaknesses |
| 24 | 24 | Develop | VM hardening | Harden the deliverable for production deployment | Running VM |
| 25 | 25 | Develop | Code Commit Logging | Logging of successful code commits, or analysis of rejected commits, which will have benefits to security and insider threat protections | -Review Comments -Source Code Weakness Findings -Version-Controlled Source Code -Security Findings and Warnings |
| 26 | 26 | Build | Build | Compile and link | Source code; dependencies |
| 27 | 27 | Build | Static application security test and scan | Perform SAST to the software system | Source code; known vulnerabilities and weaknesses |
| 28 | 28 | Build | Dependency vulnerability checking | Identify vulnerabilities in the open source dependent components | Dependency list or BOM list |
| 29 | 29 | Build | Release packaging | Package binary artifacts, VM images, infrastructure configuration scripts, proper test scripts, documentation, checksum, digital signatures, and release notes as a package. | Binary artifacts; Scripts; Documentation; Release notes |
| 30 | 30 | Build | Store artifacts | Store artifacts to the artifact repository | Binary artifacts; Database artifacts; Scripts; Documentation; |
| 31 | 31 | Build | Build configuration control and audit | Track build results, SAST and dependency checking report; Generate action items; Make go/no-go decision to the next phase | Build results; SAST report; Dependency checking report |
| 32 | 32 | Test | Unit test | Assist unit test script development and unit test execution. It is typically language specific. | Unit test script, individual software unit under test (a function, method or an interface), test input data, and expected output data |
| 33 | 33 | Test | Dynamic application security test and scan | Perform DAST or IAST testing to the software system | Running application and underlying OS; fuzz inputs |
| 34 | 34 | Test | Integration test | Develops the integration test scripts and execute the scripts to test several software units as a group with the interaction between the units as the focus. | Integration test scripts, the software units under test, test input data, and expected output data |
| 35 | 35 | Test | System test | System test uses a set of tools to test the complete software system and its interaction with users or other external systems. Includes interoperability test, which demonstrates the system's capability to exchange mission critical information and services with other systems. | System test scripts, the software system and external dependencies, test input data and expected output data |
| 36 | 36 | Test | Manual security test | Such as penetration test, which uses a set of tools and procedures to evaluate the security of the system by injecting authorized simulated cyber-attacks to the system. CI/CD orchestrator does not automate the test, but the test results can be a control point in the pipeline. | Running application, underlying OS, and hosting environment |
| 37 | 37 | Test | Performance test | Ensure applications will perform well under the expected workload. The test focus is on application response time, reliability, resource usage and scalability. | Test case, test data, and the software system |
| 38 | 38 | Test | Regression test | A type of software testing to confirm that a recent program or code change has not adversely affected existing features. | Functional and non- functional regression test cases; the software system |
| 39 | 39 | Test | Acceptance test | Conduct operational readiness test of the system. It generally includes: Accessibility and usability test failover and recovery test performance, stress and volume test security and penetration test interoperability test compatibility test supportability and maintainability | The tested system Supporting system Test data |
| 40 | 40 | Test | Compliance scan | Compliance audit | Artifacts; Software instances; System components |
| 41 | 41 | Test | Test audit | Test audit keeps who performs what test at what time and test results in records | Test activity and test results |
| 42 | 42 | Test | Test deployment | Deploy application and set up testing environment using Infrastructure as Code | Artifacts (application artifacts, test code) Infrastructure as Code |
| 43 | 43 | Test | Database functional test | Perform unit test and functional test to database to verify the data definition, triggers, constrains are implemented as expected | Test data; Test scenarios |
| 44 | 44 | Test | Database non- functional test | Conduct performance test, load test, and stress test; Conduct failover test | Test data; Test scenarios |
| 45 | 45 | Test | Database security test | Perform security scan; Security test | Test data; Test scenarios |
| 46 | 46 | Test | Test configuration audit | Track test and security scan results; | Test results; Security scan and compliance scan report |
| 47 | 47 | Test | Test configuration control | Generate action items; Make go/no-go decision to the next phase. (There may be several iterations for several tests across stages) | Version controlled test results |
| 48 | 48 | Release and Deliver | Release go / no-go decision | This is part of configuration audit; Decision on whether to release artifacts to the artifact repository for the production environment. | Design documentation; Version controlled artifacts; Version controlled test reports; Security test and scan reports |
| 49 | 49 | Release and Deliver | Deliver released artifacts | Push released artifacts to the artifact repository | Release package |
| 50 | 50 | Release and Deliver | Artifacts replication | Replicate newly release artifacts to all regional artifact repositories | Artifacts |
| 51 | 51 | Release and Deliver | Ops Team Acceptance | Testing on the delivered artifacts to ensure that they meet operational requirements | Release package |
| 52 | 52 | Release and Deliver | Configuration Integration Testing | Accepted Release Package | |
| 53 | 53 | Release and Deliver | Development Test and Operational Test | Known CVEs, privacy requirements, security requirements, and potential threats | |
| 54 | 54 | Release and Deliver | Parallel government testing | Feature requirements and performance requirements | |
| 55 | 55 | Release and Deliver | Delivery Results Review | Configuration results and Recommendations | |
| 56 | 56 | Deploy | Artifact download | Download newly release artifacts from the artifact repository | Artifact download request |
| 57 | 57 | Deploy | Infrastructure provisioning automation | Infrastructure systems auto provisioning (such as software defined networking, firewalls, DNS, auditing and logging system, user/group permissions, etc.) | Infrastructure configuration scripts / recipes / manifests / playbooks |
| 58 | 58 | Deploy | Create linked clone of VM master image | Instantiate VM by creating a link clone of parent VM with master image | VM parent; New VM instance parameters |
| 59 | 59 | Deploy | Post-deployment security scan | System and infrastructure security scan | Access to system components and infrastructure components |
| 60 | 60 | Deploy | Post-deployment checkout | Run automated test to make sure the important functions of system are working | Smoke test scenarios and test scripts |
| 61 | 61 | Deploy | Database installation | Database software installation; Cluster or high availability setup | Artifacts in the repository; data |
| 62 | 62 | Deploy | Database artifact deployment | Database artifacts deployment and data loading | Artifacts in the repository; data |
| 63 | 63 | Operate | Backup | Data backup; System backup | Access to backup system |
| 64 | 64 | Operate | Scale | Scale manages VMs/containers as a group. The number of VMs in the group can be dynamically changed based on the demand and policy. | Real-time demand and VM performance measures Scale policy (demand or Key Performance Indicator (KPI)threshold; minimum, desired, and maximum number of VMs/containers) |
| 65 | 65 | Operate | Load balancing | Load balancing equalizes the resource utilization | Load balance policy Real time traffic load and VM/container performance measures |
| 66 | 66 | Operate | Feedback | The Second Way: Feedback | Technical feedback as to “is the system built right” and operational feedback as to “was the right system built” |
| 67 | 67 | Monitor | Compliance Monitoring (resources & services) | Monitor the state of compliance of deployed cloud resources and services against NIST SP 800-53 controls | |
| 68 | 68 | Monitor | Compliance Monitoring (COTS) | Monitor the state of compliance of deployed COTS against STIGs | |
| 69 | 69 | Monitor | Logging | Log system events | All user, network, application, and data activities |
| 70 | 70 | Monitor | Log analysis | Filter or aggregate logs; Analyze and correlate logs | Logs |
| 71 | 71 | Monitor | Log auditing | Ensure possession of the logs and that aggregation is performed correctly | Logs |
| 72 | 72 | Monitor | System performance monitoring | Monitor system hardware, software, database, and network performance; Baselining system performance; Detect anomalies | Running system |
| 73 | 73 | Monitor | System Security monitoring | Monitor security of all system components Security vulnerability assessment System security compliance scan | Running system |
| 74 | 74 | Monitor | Asset Inventory | Inventory system IT assets | IT assets |
| 75 | 75 | Monitor | System configuration monitoring | System configuration (infrastructure components and software) compliance checking, analysis, and reporting | Running system configuration; Configuration baseline |
| 76 | 76 | Monitor | Database monitoring and security auditing | Database performance and activities monitoring and auditing | Database traffic, event, and activities |
